General Assumptions & Testing Methodology
4. Security
Management Deployment
6. Software
Blades Configuration
10. Anti-Bot
& Anti-Virus Blades
11. Application
Control & URL Filtering Blades
12. Data
Loss Prevention Blade
Introduction
This
document presents the general assumptions & performance testing
methodologies taken for the Appliance Selection Tool.
This
document is being updated periodically with new methodologies upon new features
and requirements.
General
Assumptions
Performance forecasts
-
All Recommendations are based on Check Point R75.40 Release.
-
Performance forecasts are based on typical customer deployment scenarios, variations can be
expected upon deployment at different customer networks.
Blade Inspection Policy
-
In order to apply ‘Internet only’ traffic to the blade inspection, you
should validate the inspection scope on each blade policy.
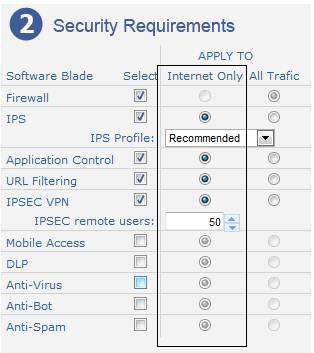
Appliance
Selection tool – Security requirements step.
Testing Methodology
Lab setup
This section provides general
information about the topologies and test-beds of the performance tests for the
Appliance Selection Tool. During the performance tests, the DUT (device under
tests) can contain the maximum possible network interfaces
connected.
1.
Traffic Blend
1.1 Internet
Blend
-
Represents the type
of Internet traffic, security appliances handle on a day-to-day basis.
-
Based on customer research conducted by Check Point
performance labs.
-
Consists from the following Streams/Protocols: HTTP;
HTTPS; SMTP; DNS; POP3; FTP; Telnet.
-
The majority of the traffic is Internet Access (HTTP).
Full traffic blend description
|
Protocol |
Action |
Details |
Distribution |
|
HTTP |
Amazon Home Page |
HTTP GET of Amazon Home Page, 676K |
16% |
|
Yahoo Home Page |
HTTP GET of Yahoo Home Page, 292K |
16% |
|
|
Facebook Home Page |
HTTP GET of Facebook Home Page, 271K |
16% |
|
|
Google Search |
HTTP GET of Google Home Page, 41K |
17% |
|
|
Google Mail |
HTTP GET of Gmail index.html file, 21K |
2% |
|
|
HTTP Post |
100K PDF file |
1% |
|
|
Total HTTP Protocol |
68% |
||
|
SMTP |
SMTP 17K |
MIME Message with PDF Attachment file |
7% |
|
SMTP 100K |
MIME Message with MS word Attachment file |
6% |
|
|
Total SMTP Protocol |
13% |
||
|
HTTPS |
HTTPS 10K |
HTTPS GET of 10K file |
5% |
|
HTTPS 100K |
HTTPS GET of 100K file |
5% |
|
|
Total HTTPS |
10% |
||
|
Other Protocols |
DNS |
DNS Query |
6% |
|
POP3 |
Message size: 256-512 bytes |
1% |
|
|
Telnet |
Login; cd /disk/images; ls |
1% |
|
|
FTP |
FTP get, 1MB file |
1% |
|
|
Total Other Protocols |
9% |
1.2 Data Center Blend
-
Check Point empirical study found the following common
applications in the Data Center: Web Services, File Stores,
Authentication Services, Line-of-Business Applications, Custom Applications and
Data Intensive Applications.
-
Consists from the following Stream/Protocols : HTTP;
HTTPS ; SMTP ; SMB_CIFS ; SQL ; NFS ;
SMB_DCERPC ; Oracle ; DNS ; LDAP ; SSH ; FTP.
-
Typical Data Center traffic blends consume around 20% more
SPU power than Internet traffic blend
2.
Topology Diagram
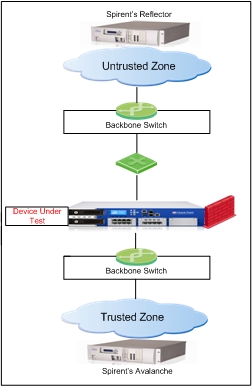
3.
SecureXL & CoreXL
- Check Point SecureXL – Enabled.
-
Check Point CoreXL – Enabled (Out-of-the-box configuration).
3.1 SIM Affinity
Performance Pack is able to utilize architecture
of multiple CPUs and Cores. In order to optimize results, Performance Pack
attaches different NICs’ IRQs, to different CPUs or cores. This process is done
automatically and by default by Performance Pack.
-
For these performance tests we used manual assignment in order to achieve maximum results.
4.
Security Management Deployment
-
Standalone
Deployment - Where the gateway and the Security Management
server are installed on the same machine.
-
Distributed
Deployment - Where the gateway and the Security Management
server are installed on different machines.
5.
Security Policy
-
Firewall Rule Base
·
100
Firewall Rules.
·
Traffic
is evenly distributed amongst these rules.
-
Logging
·
All
rules are configured to send a log record per connection.
- Network Address Translation (NAT)
·
Perform
on all connections that pass through the Security Gateway.
6.
Software Blades Configuration
7.
IPS Blade
- Profile Assignment:
Pre-defined Profile: “Recommended_Protection”.
- Protection Scope:
Protect Internal Hosts only.
8.
Mobile Access Blade
- Simulating Mobile
Users connecting securely to corporate resources through SSL VPN
Portal.
- Simulated Web Application: Outlook Web
Access.
- Simulated OWA usage profile:
Heavy Usage.
9.
IPSEC
VPN Blade
- Simulating VPN Remote Access Clients.
- VPN Kbps per User: 20.
- Encryption Algorithm:
AES128
10. Anti-Bot & Anti-Virus Blades
-
Out-of-the-box configuration.
- According to the Anti-Bot and Anti-Virus Policy.
- Up to date Signatures.
11. Application Control & URL
Filtering Blades
- Out-of-the-box
configuration.
-
Up to date Signatures.
12. Data Loss Prevention Blade
- Default Deployment - Uses the Data Loss Prevention
policy provided Out of the Box.
-
Out-of-the-box Data Loss
Prevention with a basic policy (DLP Software Blade comes with a
large number of built-in data types that can be quickly applied as a default
policy).
-
DLP Portal and Mail Relay
Activated.
-
Default Applied Protocols:
Email (Scan outgoing Emails).
